Trusted digital identities are the key to future digitalisation

Steinbeis M&A, represented by Alfred Dietel and Christian von Staudt, accompanied the mySaveID team of targens GmbH over a period of 18 months from the verification and optimisation of the business plan to the spin-off of the business unit and the sale to msg in April of this year. Karsten Treiber, Managing Director of mySaveID at msg, and Steinbeis M&A discuss the importance of decentralised, digital identities (Self-Sovereign Identity = SSI) for the ongoing digitalisation of many business areas in almost all industries.
Holistic transaction advice by entrepreneurs for entrepreneurs!
Steinbeis M&A www.steinbeis-finance.de/en offers its clients a comprehensive and professional range of consulting and services in the areas of (1) Mergers & Acquisitions (2) Buy-and-Build, (3) Strategy and (4) Capital Advisory, across all industries. Clients are in particular medium-sized entrepreneurs, companies and groups of companies in Germany and abroad, but also international groups that want to establish themselves in the SME market.
Steinbeis M&A currently has 13 partners who have completed well over 200 successful transactions in recent years. Steinbeis M&A with offices in Frankfurt, Stuttgart, Hamburg, Cologne, Berlin, Munich, Karlsruhe, Vienna (A), Zurich (CH), Palma (ES) and London (UK) is an independent consulting firm of the Steinbeis Group.

Partner Steinbeis M&A
Alfred Dietel: Why are trusted digital identities so (immensely) important?
Karsten Treiber: Until now, the implementation of digitisation projects has often been subject to legal, social and especially statutory limits, so that the digital transformation ends at the company boundary. Yet it is precisely the cross-company processes that offer a high potential for optimisation.
The management of company authorisations and data in the external relationship is particularly time-consuming. Trusted authorisations can initiate digitalised processes that make adjustments to administrative tasks and competences in corporate structures much easier, faster and more cost-effective.
Christian von Staudt: How can we visualise the topic of digital identity?

Steinbeis M&A
Karsten Treiber: A digital identity can be used to clearly identify a company, a person or an object in the virtual world as well as in real life. In real life, this is often done with an identity card or a certificate.
Typical characteristics of a person’s real identity are, for example, the name, address and date of birth or also a fingerprint, a picture of the face and the body size. The best-known attributes of a digital identity so far often consist only of a user name and password and are correspondingly (highly) risky. This is exactly what we want to change.
Alfred Dietel: Meanwhile, cyberattacks on government agencies and hacker attacks on companies are constantly in the news. How can we protect ourselves from this and what developments help?
us in this?
Karsten Treiber: In order to exclude misuse, it must be ensured that access is only through a clearly identifiable data form of a digital image of a real person, company or object. For some time now, real persons have been obtaining their Digital Identity in the virtual world by means of data processing and encryption. Some procedures have little security, such as simply registering usernames and passwords on a website. Other procedures require increased security. For example, additional PIN processes of chip cards or TAN generators have been introduced, or two-factor authentication as well as biometric recognition data. Opening an account through a video identification process, for example, uses real identification features of the natural person on the basis of the present
identity card to create the digital identity of the account holder.
Christian von Staudt: That already sounds very safe and mature. What are the problems with these procedures or why are they not already being used everywhere?
Karsten Treiber: The proof of one’s own digital identity must be fast, convenient and secure in order to be used by a broad mass. This is often not yet the case today. The improved access procedures mentioned are extremely cumbersome, time-consuming and also error-prone for most users.
Also, these methods are at best suitable for the correct identification of persons or their transactions, but not for objects. In addition, it is preferable to store only a small amount of identification data in places over which the user has no control. It is also important that a person can identify himself to a body without third parties finding out. Unfortunately, current procedures do not fulfil these security features and are also not very user-friendly. This leads to many companies continuing to rely on mainly classic procedures, often limited to one use case, when logging in via company log-ins. But can one be sure that it is really the authorised person and not an attack?
Unauthorised third parties could not only access the internal company network and view information, but also initiate transactions or manipulate e-mails.
Alfred Dietel: In the near future, what are the solutions for the ongoing digitisation of transactions?
Karsten Treiber: At the heart of this is the desire for decentralised use of trustworthy identity data, a trustworthy digital identity. One driver of this type of data use comes from the requirements of Distributed Ledger Technology (DLT), one of the best-known examples is blockchain technology, which is used, for example, for the creation (mining) of Bitcoins. Here, transactions and objects can already be processed and logged in an unchangeable way.
The starting point of this procedure is IT algorithms that encrypt data in a decentralised, transparent and secure manner. The English term “ledger” means a journal or ledger for the purpose of keeping records. The trust and transparency of DLT lies in the fact that a copy of the ledger is distributed to each authorised participant (node) in the network and each node views the ledger, checks it and detects and discards any tampering or attempted fraud in the transaction process (Figure 1).
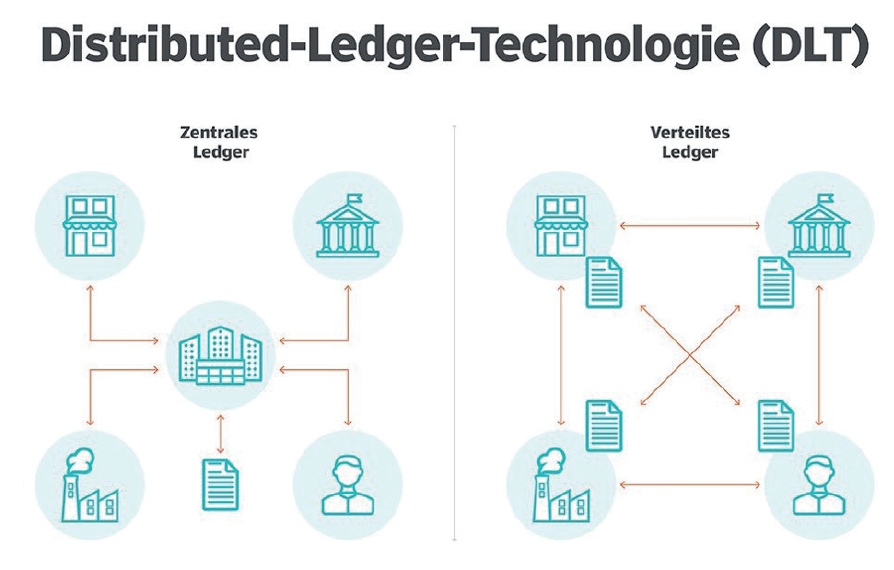
An essential component of the technical processes of this technology is the decentralised digital identity, also known as Self-Sovereign Identity (SSI). On the one hand, this leads to data sovereignty of the user, on the other hand, it enables more efficient data processing.
Unlike most established IT processes, the user manages their Digital Identity themselves without depending on a third party to store the user’s personal data.
Instead, certified, trustworthy trustees (trust service providers or trust services) provide the user with a one-time, trustworthy confirmation of certain personal identity characteristics such as name, address or age. He can then use these, without further consent, through the trust service to identify or authenticate a transaction. The advantage of a self-sovereign identity lies on the one hand in the decentralised use of the data, but on the other hand, above all, in the fact that the user is not restricted in the data that a provider allows to be managed. The data of a digital identity can grow at will.
Christian von Staudt: Could you give us a more tangible account of the use of a self-sovereign identity?
Karsten Treiber: To manage the identity, you need an access software (called a wallet). This stores all identity attributes in encrypted form.
The user can now have identity attributes issued or confirmed by third parties. These can be, for example, the data of the company or the data of the identity card. We refer to these attributes as the core identity. Depending on the issuer of the confirmation, different qualities are achieved for the reuse of the identity. After that, any other attributes can be recorded that relate to the core identity. These can be, for example, the residents’ parking permit or the club membership card.
Alfred Dietel: Which areas of business processes will mySaveID from msg support in the future?
Karsten Treiber: In principle, we focus on solutions for confirmed personal and corporate identities. Our technology makes it possible to create and manage trustworthy digital identities (according to eIDAS and eIDAS 2.0*) in the B2B sector quickly, securely as well as cost-effectively. As a complete solution, our offer takes over all services from the creation and administration to the release of identity data to third parties and the use of qualified electronic signatures as well as the seamless integration into the business processes and systems of our customers. Further application possibilities exist primarily in the area of the Internet of Things (IoT), as in the future machines or companies will also be able to identify themselves and thus make numerous processes more efficient and cost-effective (e.g. autonomous delivery and production processes, autonomous driving, etc.).
Christian von Staudt: Could you give us an insight into the implementation of mySaveID products?
Karsten Treiber: So far, competitors only offer partial functionalities. In order to combine the offers in a way that is necessary for fully digital business processes, the customer has to register anew for each offer. This creates media discontinuities.
mySaveID combines the functionality necessary for a business process in a trustworthy, supervised service and creates added value for users and networks without media breaks.
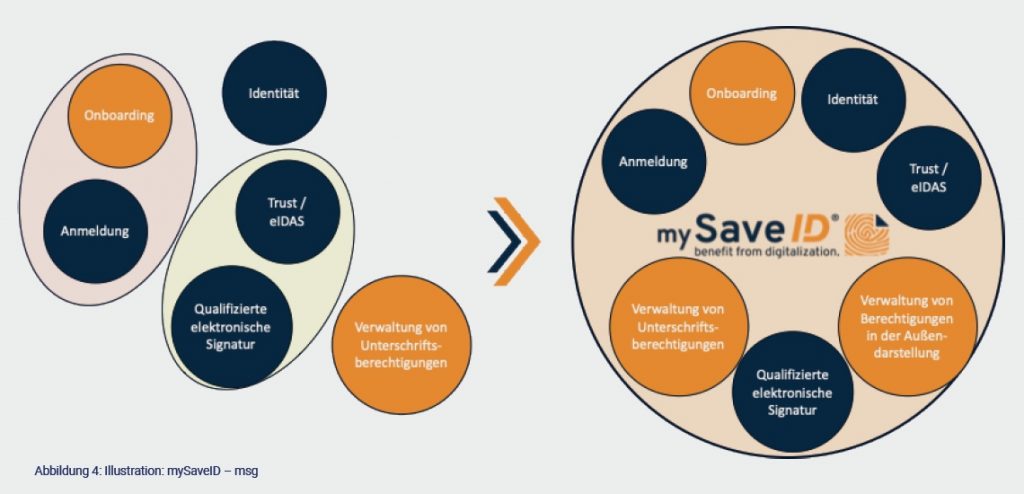
The essential products of the service portfolio according to eIDAS include the qualified electronic signature, the seal and the time stamp, which can be seamlessly integrated and used in the digital processes of our customers. The mySaveID service is designed to be technology-independent and can be integrated into existing applications, platforms or networks via standardised interfaces. Furthermore, it is compatible with a wide range of distributed ledger technologies.
Alfred Dietel: Thank you very much for giving us these insights into the prerequisites for further progress in the digital transformation. In summary, without trustworthy digital identities, any progress towards autonomous processes is almost impossible or inefficient, or has significant security flaws. The need for digital trust service providers, such as my-SaveID from msg and their products, is coming to the forefront of the digital transformation.



